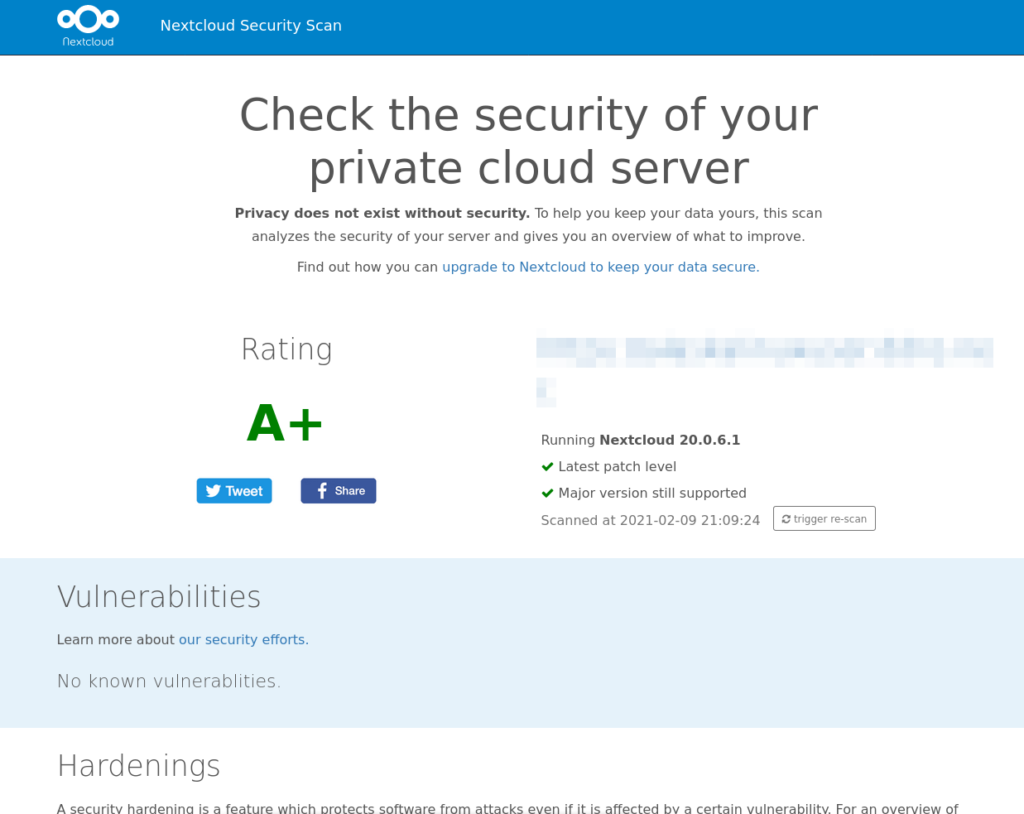
One really important part of having a home server is making sure that your server is secure. I want to start this by saying, I am not a security expert. However, I found some great tools available to help me do this. One of the best tools out there is using a vulnerability scanner to see if your server has any known weaknesses. A few that you might consider are SSL Labs, Pentest Tools.com, and if you are using a NextCloud server, NextCloud Security Scan.
When it comes to hosting my own NextCloud, it made sense to start with a quick check of my setup with the NextCloud Security Scan. If you try it, pay attention to the report in the areas of vulnerabilities and hardening. In each category, it will tell you if there is something disabled that should be enabled, or vice-versa. Your hardening report should have green check boxes for things like: Brute-force protection, CSPv3, Same-Site-Cookies, Password confirmation, Checks passwords against the “HaveIBeenPwned” database, __Host-Prefix, and that App passwords can be restricted. Most of these should be enabled by default on your NextCloud instance, but it’s good to double check with this scanner. Any issues that you find here can be quickly remedied by following the guides to NextCloud Server Hardening on their website.
Now that I’ve checked what I’m serving up, it seemed like a good idea to check my certificates with places like SSL Labs. This is pretty handy because the report will show what encryption methods, what TLS versions, and what certificates you have for your site. It will show you if you are using weak TLS versions, or if your certificates are about to expire (or already have), and will give you an overall score. This is not specific to your NextCloud server, but will show you things you might want to change about your web server.
Finally, I used a vulnerability tester, in this caseI used Pentest Tools. Places like this will show you any vulnerabilities you may have. Things like querying your web server, whether Apache or NginX or something else, and see if there is any known issues logged in the NIST vulnerability databases about your web server that can or have been exploited. It also shows what header information you are returning and that may be useful to attackers if they know your operating system or server information. It is possible to change these headers on your system, either to be blank, or to lie about what you are using to purposely mislead attackers, such as using tools like mod_headers in Apache.
Ultimately, the best thing you can do is keep your system up to date. It may also be a good idea to obscure your web server and operating system information to make software specific attacks more difficult. You can read more about that on OWASP’s website. You also might want to set up encryption for data at rest on your server, which NextCloud explains on their website. You do have to be careful though, depending on your use cases, some encryption may affect or disable certain features, so be sure to give it a thorough read before you apply it.
Again, I am not a security expert, just showing some of the things that I checked out for myself.
Linux – keep it simple.