Okay, I’m not really much of a ‘hacker’ in the sense that most people think of. I don’t break into things, crack passwords, etc. However, I do like to tinker. Recently, my co-workers and I decided to purchase and try out these handy new “smart” power cords: the IPLC M4 CORD (M4-15-2S) [1].
Note:
While plugging in your vehicle may sound odd to some of my readers, here in Alaska it is so cold, that your vehicle will not start when you need to drive it somewhere. So, when it is -40 F/C (both coincide at that temperature), you need to heat the vehicle engine up first, and we typically do this with electric heaters hooked to the engine block. The problem is, if you want to go to work at 5:30 AM, then you need to plug in the vehicle 3-4 hours prior to that to get it warm enough. Since nobody wants to get up at 1 AM to plug in their vehicle, most plug it in at night before bed, but this wastes electricity and costs you more money on your electric bill. Most of us use a timer circuit that turns on the power at a certain time. This works great, except every power outage either resets your timer, or at least gets it off of the correct time.
What a cord like this M4 does, is it first has a delay, in this case of either 3 or 6 hours, depending on your setting. Then, once the delay is over, it starts turning the power on and off, in accordance with how cold it is. So, if it is too warm, it will not turn on the power to the heater, to save you money. If it is cold enough, but not -30 F, then it will cycle the power on and off in increments to keep your engine warm, but not leave it on all the time and waste electricity. Very handy, and they work rather well. No need for a timer, and if the power goes out, it is smart enough to assume that the delay time is over and just start power cycling based on temperature.
For every action there must be a reason to pursue that course of action. And this case is no exception. My co-worker wanted to change the default delay times from 6 or 3 hours to 12 and 6 hours. So, we began to look deeper at the controller to see what we could gain. The power cord has it’s own WIFI connection so you can connect with your phone or home computer to it, and the passwords were all provided in the documentation. We didn’t have to “break in” to talk to it, since it was designed for us to connect to it.
Running nmap to check for any open ports.
First up, I wanted to see what ports were open. Sometimes manufacturers leave open ports like FTP, or telnet, SSH, or others that give you an avenue to get in. So, I check all possible ports, rather than just the standard, just in case they used a non-traditional port number for something.
alaskalinuxuser@alaskalinuxuser-OptiPlex-790:~$ nmap 10.10.10.1 -p1-65535
Starting Nmap 7.80 ( https://nmap.org ) at 2022-12-30 06:41 AKST
Nmap scan report for 10.10.10.1
Host is up (0.035s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 40.49 secondsSo, one port was open, port 80, and that’s it. So, kudos to the manufacturer, either for security or otherwise, it didn’t have any of the usual open ports allowing entry.
Connecting to the web gui.
Overall the web gui seemed pretty simple and straightforward. Just a few buttons to change between the gas or diesel profile, and to hook to your home WIFI network. I inspected it with Firefox, but didn’t see anything unusual about it. All of the buttons ran scripts or were links to other local web pages. I thought I would check for robot.txt files and sitemap.xml files, but didn’t find any, so no hidden pathways or avenues there. Although later I did find a way to reboot the device and get to a special admin web page, but more on that later. Here is a picture of the web gui:
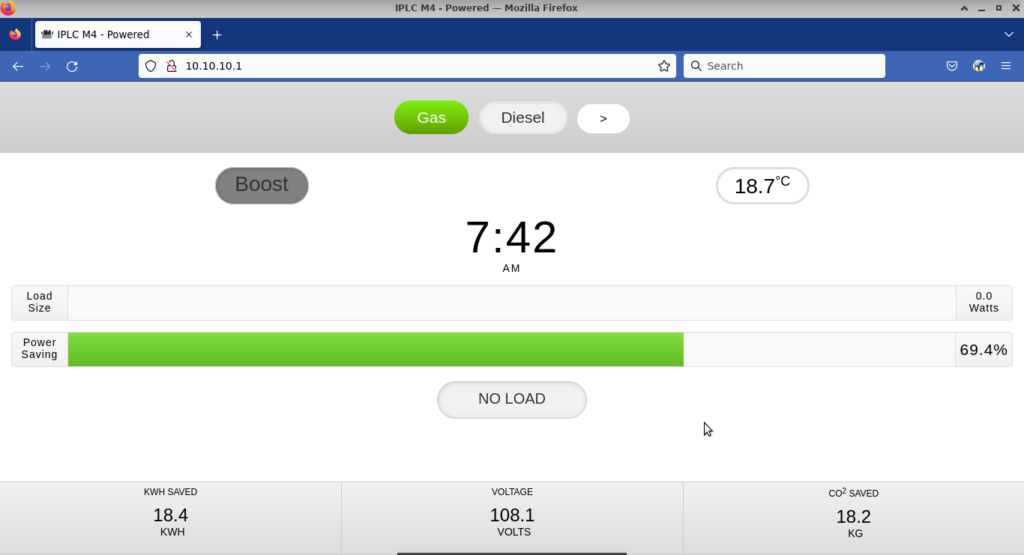
Using curl to download all the web pages.
Having seen all I could in the browser, I used curl to download the main html file. From there, I saw the buttons linked to other pages, so I downloaded them as well using curl and their href location. Below is an example.
alaskalinuxuser@alaskalinuxuser-OptiPlex-790:~$ curl 10.10.10.1 > index.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 12233 100 12233 0 0 197k 0 --:--:-- --:--:-- --:--:-- 202k
<body onload='aRP(3000, "/dd.stat");'>
<header>
<a id="m4Profile1" onClick="location.href= '/DoGAS';" class="schedule">Gas</a>
<a id="m4Profile2" onClick="location.href= '/DoDIESEL';" class="schedule">Diesel</a>
<a onClick="location.href= '/doset';" class="schedule">></a>
</header>
<div class="body">
<div class="measure">
<div class="grid">
<div class="equal">
<a id="m4Boost1" onClick="location.href='/BOOST';" class="boost">
Boost
</a>
</div>
<div class="equal">
<a onClick="location.href='/TOGT';" class="temp">
<span id="m4Temp">?</span><sup>°<span id="m4TempUnits">?</span></sup>
</a>
</div>
</div>
</div>
<div class="clock">
<span id="timeData">?:?</span>
<div class="bottom"><span id="timeAmPm">?</span></div>
</div>What I did find was that there was a ‘reset’ page that is not reachable normally, because the button was commented out, but that you could call it directly and it would reboot the device. However, it didn’t bring you to any special new pages, nor seem to do anything, so it was just an interesting tidbit. All told, I found seven web pages and one icon, called favicon.ico, which is used by the web browser to display the icon for the web pages. Nothing too noteworthy.
Using netcat to check port 80.
Feeling a bit froggy, I then decided to use netcat (nc) to check port 80. Turns out, this was very fortuitous!
alaskalinuxuser@alaskalinuxuser-OptiPlex-790:~$ nc 10.10.10.1 80
CFGdbAddr: 00003D00
ready
OK
OK
OK
OK
OK
0,CONNECT Time OUT
M210dbAddr: 00007300
test
Date: 00006228 Time: 00152047
%%
help
?
%% ?
v - Serial Number, JohnDra, and Code Ver.
A - Get Ambient Light
P - Get Proximity
F - Set R,G,B
G - Get Gravimetric data (accelerometer)
R - RESET to BOOT
S - Show Status
V - VIEW MEM 1KB
L - Load ON/OFF
w - Send WIFI directly
o - Get Proxy Value
i - invalidate caches
j - get CRC 0-Iflash 1-SRAM, 2/3 QSPI
N - Get VS,VL,IL,PL,QL
W - SET Offsets
H - Write Cal Flash page0
I - Erase Cal Flash sector0
C - Cal VL = VS
O - adjust Proximity values
K - PROXY CONFIGURATION
U - match Vs to VAC sent
E - ERASE FLASH MEMORY
Y - XIP ON/OFF
copyright 1995-2021 Vantera Incorporated. ALL RIGHTS RESERVED.
%% And just like that, we were in. I found that this was actually a telnet like function, and I tested it with telnet, which “worked better”, as it was the expected format and escape character, etc. But nc worked very well also. The menu was gained by pressing the “?” question mark character, and that proved very helpful. However, I found that there were other, unlisted commands as well. Also, the commands are case sensitive, and using the wrong case may be a different command entirely. Here are other commands I found:
%% f
Whole DBase Erased, awaiting reset.
%% g
dbase started..
VdbAddr: 00010000
Wave dbase started..
WdbAddr: 00080000
%% g
dbase stopped at: 00010000
VdbAddr: 00010000
Wave dbase stopped at: 00080000
WdbAddr: 00080000
%% M
IL: 07E6
Isense offset done
%% p
KTAU : 0.0170
Rtheta : 10.0000
Tcomp : 0.0000
tP : 0.0000
%% Q
(Did not return ? character, so it did something, just not sure what.)
%% t
Date: 00006228 Time: 00230430
%% u
(Did not return ?, and did not return you to the prompt, so it did something, but also seemed to lock it up. The green flashing color led started flashing yellow then green over and over again. Had to power cycle unit to use telnet/nc again.)
No function = a,b,B,c,d,D,e,h,J,k,l,m,n,q,r,s,T,x,X,y,z,Z,1,2,3,4,5,6,7,8,9,0
Also, no punctuation mark or special character, other than ? seemed to have any function.
So, the completed menu should look like this:
A - Get Ambient Light
C - Cal VL = VS
E - ERASE FLASH MEMORY
f - Format the database
F - Set R,G,B
g - Start/stop database writing
G - Get Gravimetric data (accelerometer)
H - Write Cal Flash page0
i - invalidate caches
I - Erase Cal Flash sector0
j - get CRC 0-Iflash 1-SRAM, 2/3 QSPI
K - PROXY CONFIGURATION
L - Load ON/OFF
M - Isense offset
N - Get VS,VL,IL,PL,QL
o - Get Proxy Value
O - adjust Proximity values
p - Some sort of sensor information
P - Get Proximity
Q - Unknown command that runs instantly but seems to have no affect.
R - RESET to BOOT
S - Show Status
t - Time and date
u - Unknown command that locks up the unit and flashes lights.
U - match Vs to VAC sent
v - Serial Number, JohnDra, and Code Ver.
V - VIEW MEM 1KB
w - Send WIFI directly
W - SET Offsets
Y - XIP ON/OFFNow that we have the completed list of commands, we will have to delve deeper into their meanings and uses. Feel free to check out the next posts for where I went from here!
Linux – keep it simple.
[1] https://www.buyiplc.com/view-product/m4
This is hardly a power cord! I would call it a smart power strip, even if there’s only one output jack. It’s so nice that regular protocols were used in the design, so anything that uses that protocol (telnet/netcat) can also interact with it! Also, interesting daemon design to use this serial connection and http server on the same port. Did the telnet client need to authenticate before issuing these menu commands?
Great question, no telnet or nc required no authentication, other than that you had to already WiFi into it, which the WiFi does require authentication, of course. I’m putting together another post with the fun things I figured out how to do once in this telnet connection as well.