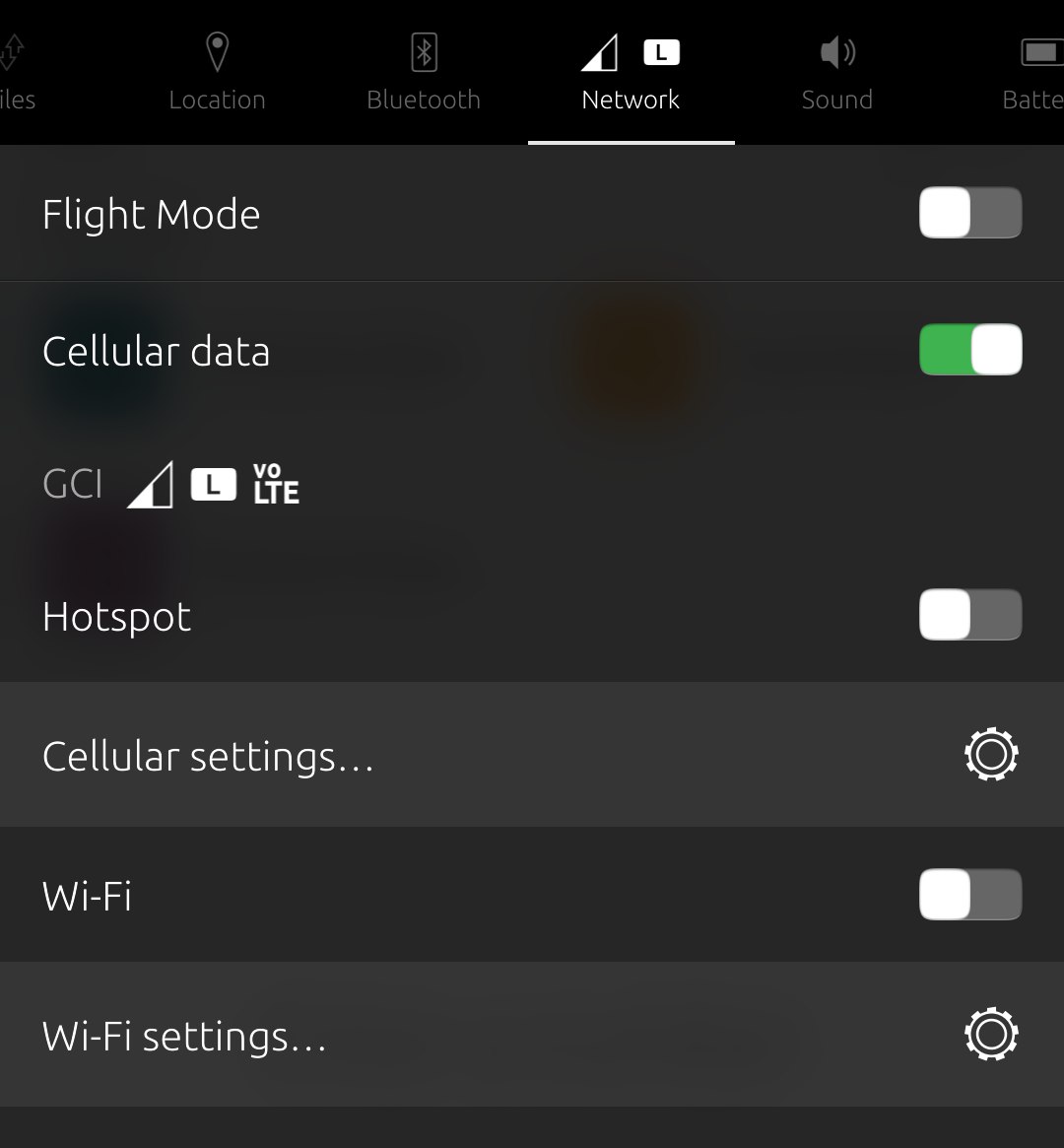
One of the biggest hangups for using Ubuntu Touch in the USA has finally been overcome! Through all the years that Ubuntu Touch has existed as an alternative to Android or iOS, it has always had one really big problem in the USA phone market: it coulnd't phone. Oh, for …